Design Challenge
In the following, we briefly summarize the design challenge. The full set of official rules is available as PDF:
Problem Setting
C-Town Public Utility (CPU) is the main water distribution system operator of C-Town (Figure 1). For many years, CPU has operated a static distribution topology. In the last year, CPU has introduced novel smart technology to enable remote data collection from sensors in the field, and remote control of actuators. Shortly after that new technology has been introduced, anomalous low levels in Tank T5 and high levels in Tank T1 were observed. A month later, a water overflow in Tank T1 occurred. While CPU personnel at the control center were able to see the anomalous readings for the first two episodes, Tank T1 overflow took place unexpectedly while the water level readings were always below the alarm thresholds and pumping operations appeared to be normal. Searching for the causes, CPU engineers suspect potential cyber-attacks for all these episodes. In particular, they are considering adversaries that are able to activate and deactivate the actuators in C-Town, as well as altering the readings of the sensors deployed in the network and the reported status of actuators, and interfering with the connections established between networked components. The participants' task is thus to develop an online alert system for cyber-physical attacks.
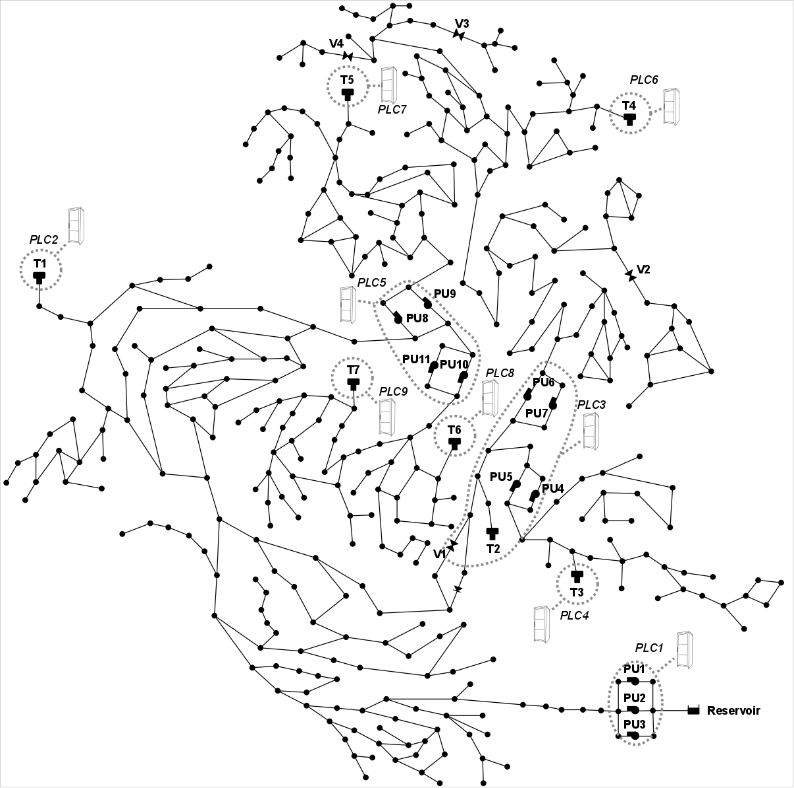
Goal of the attack detection algorithms
The primary goal of the detection mechanism is to reliably detect the presence of an ongoing attack from the SCADA readings, and to do so in the shortest amount of time. In addition, the algorithm should avoid false alarms and recognize when the threat is no longer in place. Due to the distributed nature of the WDS, an ideal detection mechanism should also be able to identify which components of the physical network are being attacked in order to facilitate and hasten incident resolution. Furthermore, the inherent interdependence of the elements in the water network should theoretically allow for the detection of anomalies even when the adversary tries to conceal his actions by altering the SCADA readings of one or a few deployed sensors. The control system will operate in the control room, based on the available SCADA data. Further information is detailed in the rules document.
Test data and evaluation criteria
A test dataset will be made available for a short time window (see schedule), during which the participants are required to run their algorithms and submit a detection report (see rules document for further details). The test dataset will contain a few months of data and contain attack instances that may differ from those of the development dataset. All algorithms will then be compared by adopting quantitative criteria based on the time-to-detection and events classification (confusion matrix).
References
- R. Taormina, S. Galelli, N. O. Tippenhauer, E. Salomons, and A. Ostfeld (2017). "Characterizing Cyber-Physical Attacks On Water Distribution Systems" J. Water Resour. Plann. Manage, doi: 10.1061/(ASCE)WR.1943-5452.0000749 (link)
- R. Taormina, S. Galelli, N. O. Tippenhauer, E. Salomons, and A. Ostfeld (2016), "Assessing the effect of cyber-physical attacks on water distribution systems," in Proceedings of World Congress on Environmental & Water Resources (EWRI).
- R. Taormina, S. Galelli, N. O. Tippenhauer, E. Salomons, and A. Ostfeld (2016), "Simulation of Cyber-Physical Attacks on Water Distribution Systems with EPANET," in Proceedings of Singapore Cyber Security Conference (SG-CRC). (link)
- Rasekh, A., Hassanzadeh, A., Mulchandani, S., Modi, S., and Banks, M. (2016). "Smart Water Networks and Cyber Security." J. Water Resour. Plann. Manage. (link)